DLL Injector Hacker 1.6.4.5 Crack
DLL Injector Hacker is a powerful software tool that has become synonymous with the world of computer security and software manipulation. It serves a specific and often controversial purpose in the realm of computing. To understand its significance and potential impact, let’s delve into the details of what Dynamic Link Library (DLL) Injector Hacker is and what makes it so intriguing.
DLL Injector Hacker is essentially a program designed to inject dynamic link libraries (DLLs) into the memory space of running processes. In simpler terms, it allows users to modify the behavior of other programs by injecting custom code into them. DLLs are collections of code, data, and resources that multiple programs can share, making them a fundamental component of the Windows operating system. By injecting custom DLLs into processes, DLL Injector Hacker can alter the way programs function, opening up a world of possibilities for both legitimate and malicious purposes.
The purpose of Dynamic Link Library Injector Hacker is multifaceted, and its usage can vary widely based on the intent of the user. Below, we will explore the primary reasons why individuals and organizations utilize this software:
- Game Modification: DLL Injector Hacker is often employed by gamers to gain an unfair advantage in online multiplayer games. By injecting custom DLLs into a game’s process, players can access cheats, hacks, and enhancements that would otherwise be unavailable. These modifications can include wall hacks, aimbots, and speed boosts, providing an unfair edge over other players.
DLL Injector Hacker Crack Download
Download Link
- Software Debugging and Reverse Engineering: Developers and security professionals use Injector Hacker as a debugging tool. By injecting custom DLLs into a program, they can analyze its behavior, trace its execution, and identify vulnerabilities or weaknesses. This process aids in reverse engineering and patching software for security purposes.
- Customization: Users may employ DLL Injector Hacker to customize the behavior of applications or games. This can involve changing the appearance, adding features, or even removing restrictions imposed by the software’s developers. Such customization can enhance the user experience.
- Testing and Troubleshooting: Software testers and quality assurance professionals use DLL Injector Hacker to simulate specific conditions or scenarios in which a program might encounter errors. This aids in identifying and rectifying issues before a product’s release.
- Malicious Intent: Unfortunately, some individuals use DLL Injector for malicious purposes, such as injecting malware or ransomware into legitimate processes. This can result in data breaches, system compromise, and other cyberattacks.
Key Features
DLL Injector Hacker boasts a range of features that make it a versatile tool for various purposes. Here are nine key features of the software, each explained in detail:
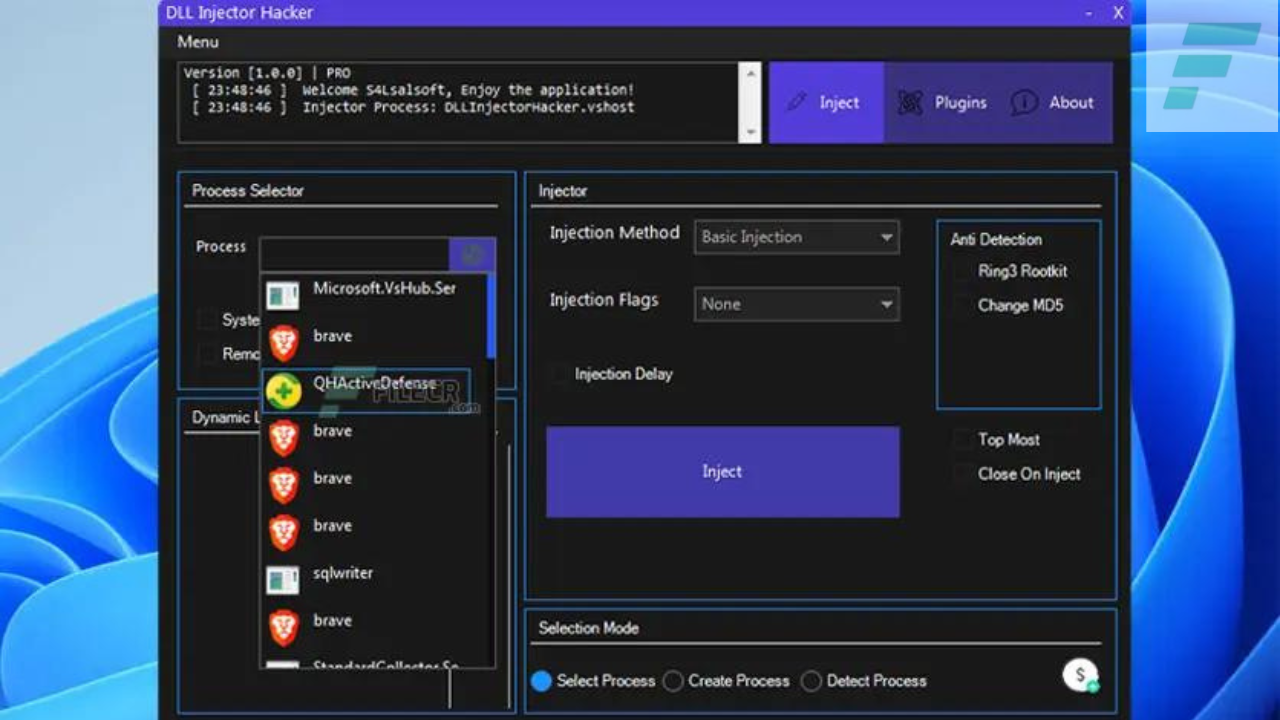
- Process Selection: DLL Injector allows users to select target processes for injection. This feature ensures that custom DLLs are injected into the correct application or game.
- Automatic Injection: Users can automate the injection process, saving time and effort when injecting multiple DLLs into different processes.
- Manual Mapping: For advanced users, DLL Injector Hacker provides manual mapping options, allowing precise control over the injection process and memory allocation.
- Injection Methods: The software offers different injection methods, such as LoadLibrary and CreateRemoteThread, to cater to various scenarios and ensure compatibility with different applications.
- Code Execution: Injector Hacker supports executing custom code within the target process, enabling modifications to the program’s behavior.
- DLL Management: Users can manage and organize their custom DLLs within the software, making it easy to select and inject specific libraries.
- Error Handling: The tool includes robust error-handling mechanisms to address issues that may arise during the injection process, ensuring stability and reliability.
- Security Measures: To prevent detection and avoid anti-cheat mechanisms in games, DLL Injector Hacker incorporates anti-detection features and anti-analysis techniques.
- User-Friendly Interface: Despite its powerful capabilities, DLL Injector Hacker offers a user-friendly interface that makes it accessible to both novices and experienced users.
What’s New?
The latest version of DLL Injector Hacker introduces several noteworthy features and improvements. Here are five key additions that enhance its functionality:
- Multi-Process Injection: The new version allows users to inject custom DLLs into multiple processes simultaneously, streamlining the modification of multiple applications or games.
- Improved Anti-Detection Techniques: Enhanced anti-detection measures have been implemented to make it even more challenging for anti-cheat systems to identify the injected DLLs, ensuring a higher level of stealth.
- Process Monitor: The software now includes a process monitor that provides real-time information about the target processes, making it easier to select the correct ones for injection.
- Custom Code Libraries: Users can now create and manage custom code libraries within DLL Injector Hacker, enabling the reuse of code across multiple injections.
- Enhanced Compatibility: The new version offers improved compatibility with a wider range of games and applications, reducing the likelihood of compatibility issues.
System Requirements
Before installing DLL Injector Hacker, ensure that your system meets the following minimum requirements:
- Operating System: Windows 7 or later
- Processor: Intel Core i3 or equivalent
- RAM: 4 GB
- Free Disk Space: 100 MB
- Graphics: DirectX 11 compatible
How to Install
Installing DLL Injector Hacker is a straightforward process. Follow these steps to get it up and running on your Windows system:
- Download: Visit the official website of Dynamic Link Library Injector Hacker or a trusted software distribution platform to download the latest version of the software.
- Run Installer: Locate the downloaded executable file and run it. Follow the on-screen instructions provided by the installer.
- Installation Location: Choose the directory where you want to install DLL Injector Hacker. The default directory is typically in the “Program Files” folder.
- Shortcut Creation: Select whether you want to create shortcuts on your desktop or in the Start menu for easy access.
- Installation: Click the “Install” button to begin the installation process. Wait for the installation to complete.
- Finish: Once the installation is finished, you can launch DLL Injector from the shortcut created during the installation process.
Conclusion
DLL Injector Hacker is a powerful and versatile tool that can serve a range of purposes, from legitimate software debugging to unfair advantage in online games. Its key features, including process selection, code execution, and error handling, make it a valuable asset for those who understand its potential and use it responsibly.
However, it’s essential to acknowledge that the software can also be misused for malicious activities, posing security risks and ethical concerns. As with any tool, its usage should be in accordance with legal and ethical standards.
The new version of Dynamic Link Library Injector Hacker brings improvements such as multi-process injection, enhanced anti-detection techniques, and a process monitor, further enhancing its capabilities and user experience. Before installation, ensure that your system meets the minimum requirements to run the software smoothly.
In conclusion, Its remains a powerful tool in the world of software manipulation, and its impact continues to evolve as it adapts to new challenges and opportunities in the ever-changing landscape of computer technology.